GA Political
SM PHONES (SECURE AND MILITARY GRADE SMARTPHONE, COMMUNICATION, ENCRYPTION)
Couldn't load pickup availability
The threat landscape is evolving. Attacks are now exploiting multiple end-points and backdoors rather than using a single attack vector.
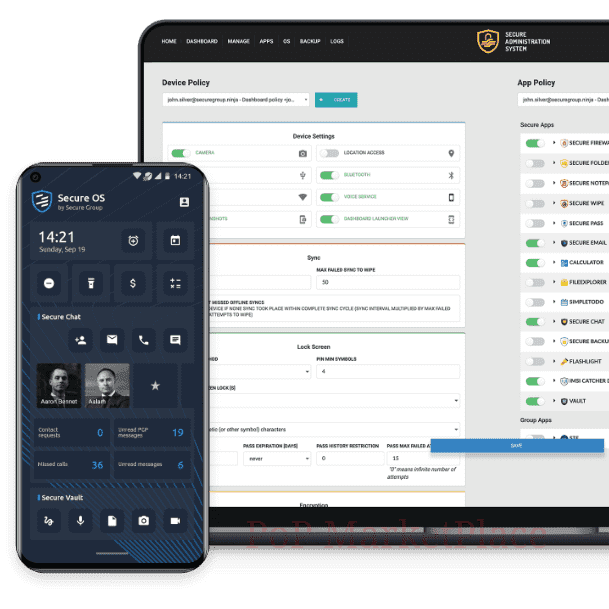
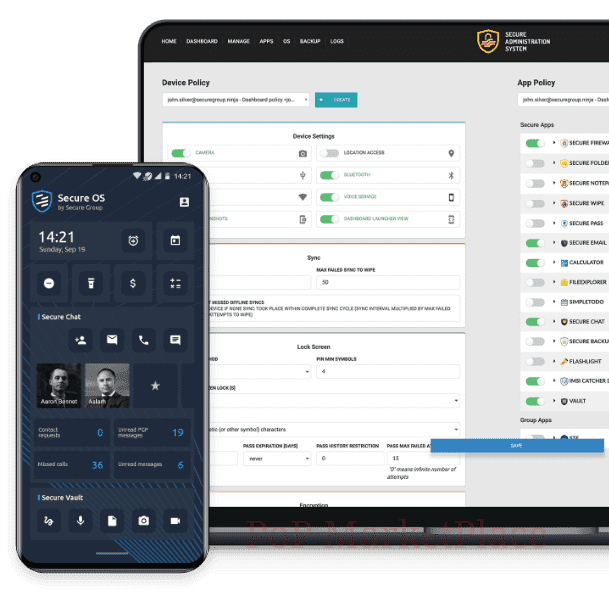
SM Phone is a smartphone platform that offers protection to mobile communications on multiple levels: device, OS, apps and, most importantly, communication. The solution incorporates recommended mobile security practices and open-source encryption protocols and standards.
Consumer-grade operating systems, such as Android and iOS, focus on user experience and extensive functionalities at the cost of thorough security. This makes such solutions easily exploitable by anyone with technical expertise and makes your data available to any third party that desires it. SM Phone is a custom operating system based on Android. It utilizes multiple defense layers to isolate, encrypt, and secure your data against any mobile threat.
360-degree protection
Attacks against mobile devices are getting more and more advanced. Different parties with malintent can quickly obtain a fingerprint of your device, find vulnerabilities, and exploit them. To prevent this, we have developed a military-grade mobile OS that is secure on every level.
Zero-attack surface
All easily exploitable entry points of modern mobile devices (Google services, GSM services, SMS, Bluetooth, NFC, GPS, and more) have been closed off in Secure OS.
Verified boot
During enrollment, a unique device fingerprint is created. On every boot, the device fingerprint is validated against a server-side copy to ensure the integrity and authenticity of the OS.
Triple password protection
The device’s storage, OS, and secure applications are all protected by separate passphrases, each set to trigger a wipe sequence if mistaken a consecutive number of times.
Multiple levels of encryption
Incoming and outgoing communication is end-to-end encrypted and transmitted over an encrypted network. All data stored on the device is secured and encrypted.
Secure KeyStore
All encryption keys are generated on the device and stored on a FIPS 140-2 certified cryptographic module. No private keys are ever shared or stored outside the device.
Trusted updates
Updates are issued and digitally signed exclusively through the Secure Administration System (SAS). Devices apply updates only after verifying the authenticity of the digital signature
Endless customization options
SM Phone allows you to create a truly unique product for your organization or target market. Customize the look and feel of your secure devices and make sure they fit your existing corporate branding or your vision for a new and disruptive security product.
- App or dashboard view
- Dark or light themes
- Custom colors
- Unique boot animation
- Integration of business-specific applications
Secure Communication Suite
Stay connected. Stay productive. Stay secure.
Mobile communication applications transfer data from one peer to another through the servers of the provider. If not encrypted, this information is readily available in plain text for all parties involved in its transfer, like your network service provider and the company that developed the application.
Furthermore, almost all mobile apps have in-built analytics that track your every move and catalog it in giant databases. Such data analytics scripts have access to your private communication, physical location, purchasing habits, and general behavioral patterns. Even encrypted mobile applications are not as safe as their developers would like you to believe. They are only as secure as the mobile stack on the device they are being used on. If malicious software finds its way on your device, it can mine data, access the application’s database, and reveal all sensitive information.
To guarantee the privacy of communication and the data security users demand, we’ve developed a set of state-of-the-art applications called the Secure Communication Suite. It includes Secure Chat, Secure Vault, and Secure Calendar. The applications protect data in transit with end-to-end encryption and securely store data-at-rest in encrypted databases.
Dimensions
Dimensions


You want in ?
You also want to be able to share your products or services on PoP ? Become a seller and join the community. Benefit from so many advantages and grow exponentially 😁